An article by Hart Ripley, Alex Lawrence, and Dan Papandrea.
It has arrived! Azure Red Hat OpenShift 4 is here and generally available; now, how do you add even more granular security and faster time to repair (MTTR) for your teams?
Sysdig, that’s how!
Wouldn’t it make sense to have a streamlined way to deploy an OpenShift cluster on Azure without the management burden? Shipping cloud applications can spider out of control quickly. When talking with our prospects and customers, we find that various platforms, multiple image repositories and disparate pipelines all contribute greatly to this. Using a platform like OpenShift can help streamline this to an extent. However, that comes with its own challenges around operational overhead for administrators and requires a deep set of knowledge to deploy and run the platform.
Leveraging Managed OpenShift on Azure (ARO) not only simplifies the operational and knowledge overhead, but it also allows companies to ship cloud applications faster by gaining access to a greater ecosystem of interconnected tools. That includes Azure DevOps for build pipelines and Azure Container Registry as a place to house images. This empowers everything OpenShift brings to the table in a cohesive and faster way. When you introduce Sysdig to this equation (OpenShift + Azure + Sysdig), you get an enterprise solution that allows you to confidently run and execute your applications out of the box.
Sysdig provides unified visibility and security for your applications on ARO. Our service-level performance and security monitoring give you deep Kubernetes, infrastructure and kernel-level insights so you can deliver reliable, secure containers. With Sysdig, you can see more and solve faster.
Get up and running with ARO!
There are a few ways to deploy a cluster. Microsoft has extended the Azure CLI “az” command toolset to include “az aro,” installed as an extension. The entire deployment workflow can also be automated for repeatability into different environments or regions using tools such as Ansible or Terraform.
Prerequisites to deployment:
1. Ensure you have the latest version of the Azure CLI.
2. Install or update the az aro extension from the Azure CLI.
3. Deploying a cluster: Official Microsoft documentation and official Red Hat documentation.
Let’s add Sysdig to the Lovefest
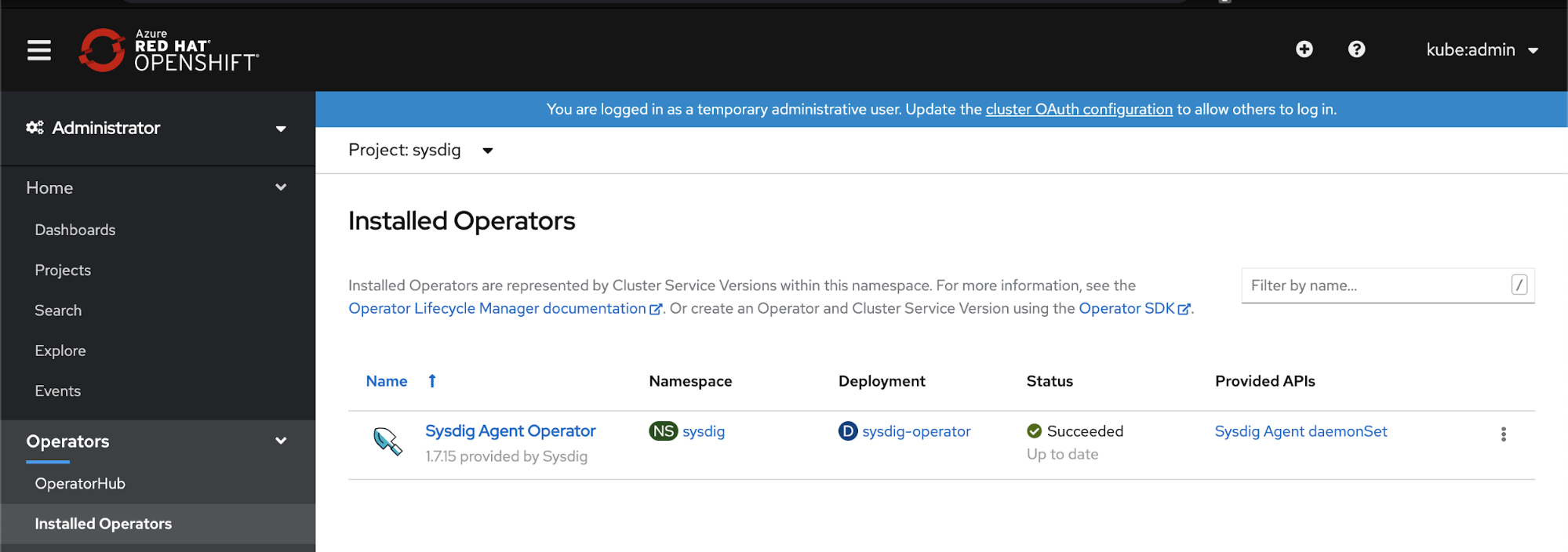
Meet Kubernetes Operators. OpenShift 4 is heavily Operator focused for deploying and managing Kubernetes applications. Integration of complementary toolsets, agents and security was previously a challenge. However, with Operators, the application lifecycle is managed, and upgrades are seamless and consistent. Not only do you get the benefit of using Operators, but application developers can also focus on consuming the platform with an improved experience and increased efficiency. Cloud-native visibility from Sysdig has landed in OperatorHub.
Additionally, base visibility into all of your Azure services from ONE portal. Adding Sysdig to this allows you a “one-stop” low resource utilization tool that gives you embedded security, additional availability and compliance capabilities.
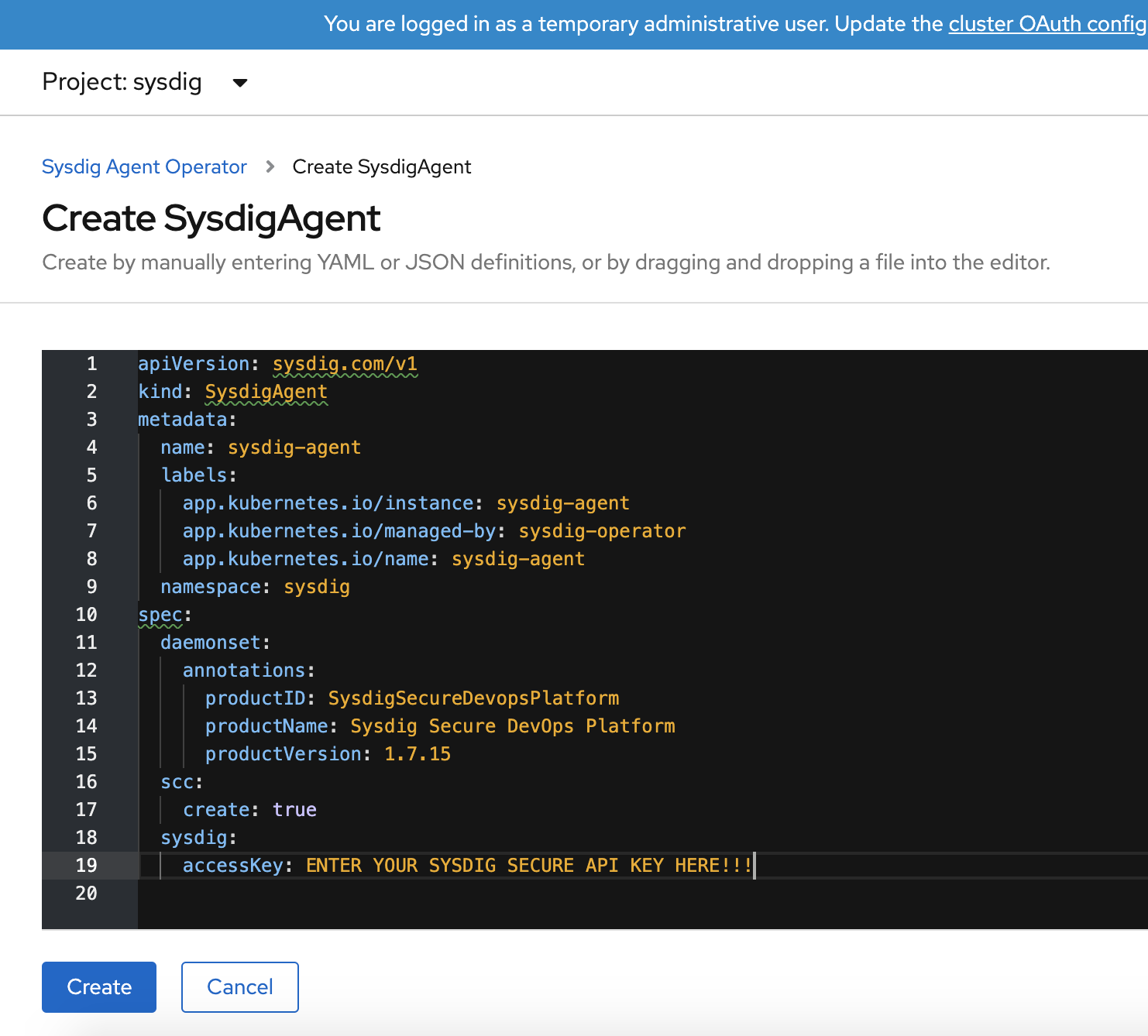
Detailed instructions for rolling out the Sysdig Agent Operator are listed in GitHub. With it, you can both install and automatically update your agent.
All you need is your access key, available from the Sysdig UI, to be able to deploy the Sysdig Agent Operator. When complete, your deployed agents will begin collecting and streaming events to Sysdig Secure and Sysdig Monitor.
Additional observability and troubleshooting using the Sysdig Secure DevOps Platform
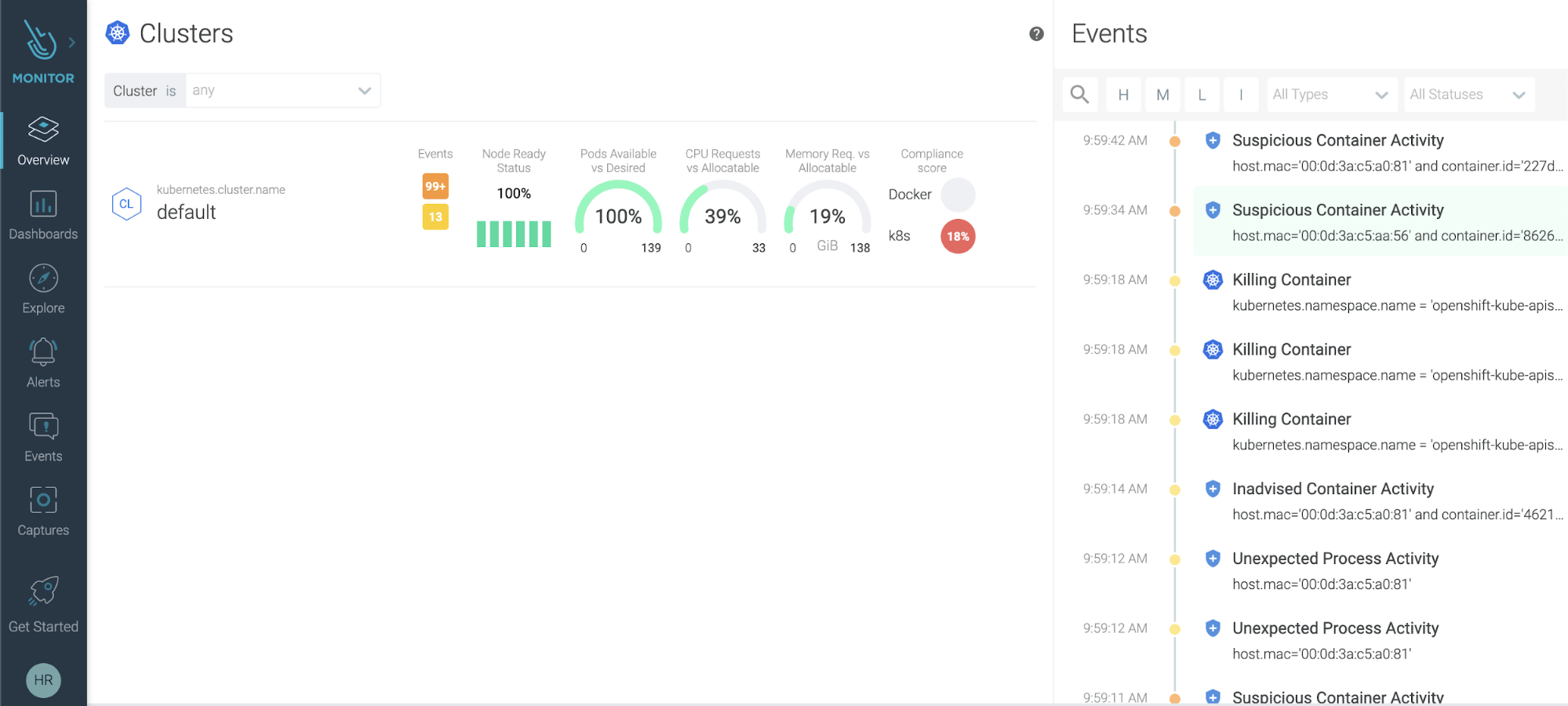
Sysdig provides you with a wide range of visibility, including Cluster level views of your Azure Redhat Openshift environment, such as resource utilization, events and compliance!
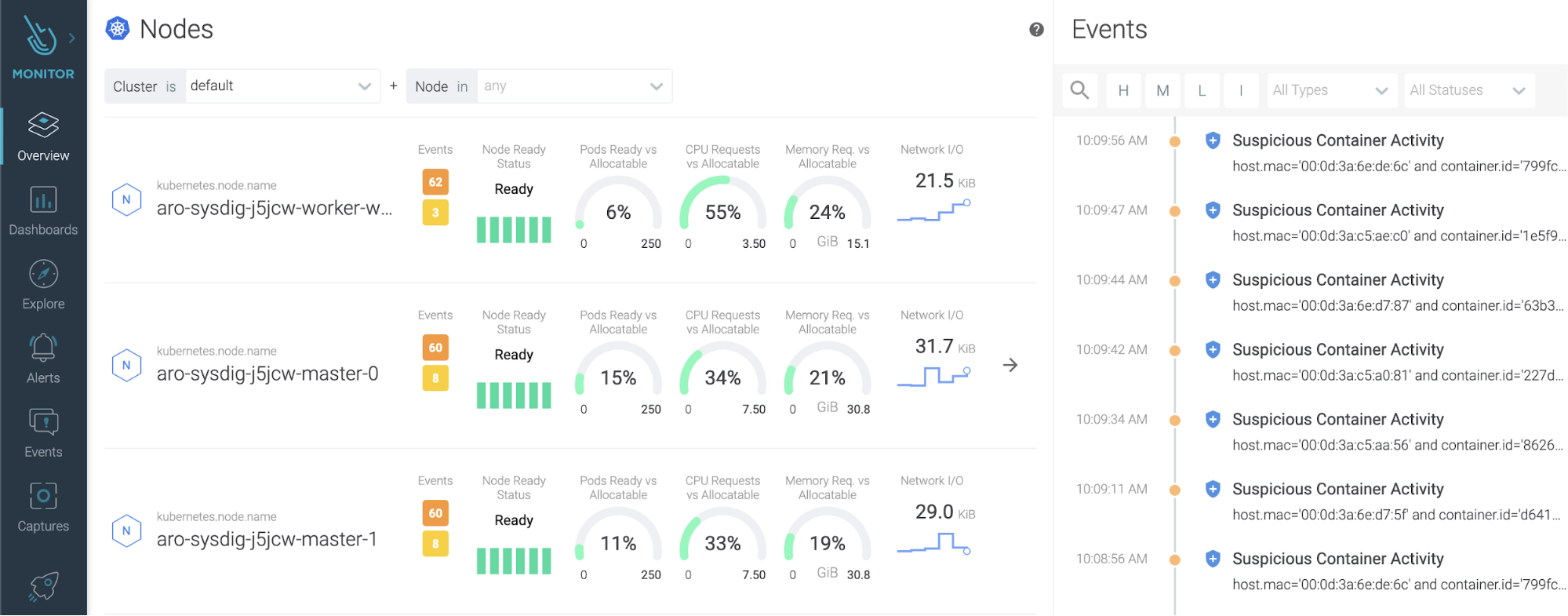
Another example of what you can observe with Sysdig is the Node level view of your Azure Redhat Openshift Cluster, also including resource utilization, events and compliance.
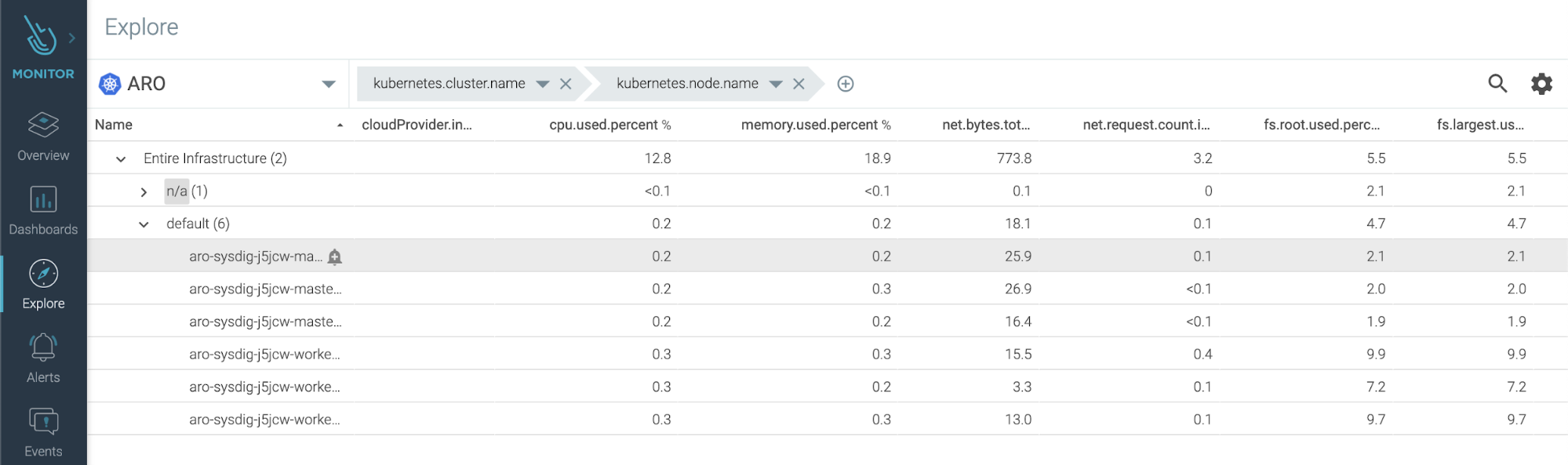
The Explore feature in Sysdig Monitor allows you to traverse your infrastructure in a way that is native to Openshift and Kubernetes. You’re able to leverage the tags in your environment to visualize your infrastructure and applications. In the example above, this is using two tags:
Kubernetes.cluster.name > kubernetes.node.name
This lets you visualize data at both the cluster level and node level. You could also do something like:
Kubernetes.cluster.name > kubernetes.namespace.name > kubernetes.deployment.name > kubernetes.pod.name > kubernetes.container.name
This allows you to view workloads within your clusters independent of which node the pods are running on, letting you visualize your services.
If you want to go even deeper, you can bring in your own tags, this could look something like:
Environment.name > region.name > kubernetes.cluster.name > etc.
In this example, we’ve created the custom tags environment.name and region.name, then applied values to those tags across objects. If you assigned values to environment.name, such as Production, Test, Development, you could segregate each at the top level, and then assign regional values to region.name, such as East, Central, West, thereby letting you further delineate the objects being visualized. This allows you to find relationships between deployments, get pointed about areas you’re investigating, or even look for anomalous/unexpected activity between regions, clusters and endpoints.
Security with Sysdig on your Azure Red Hat Openshift environment
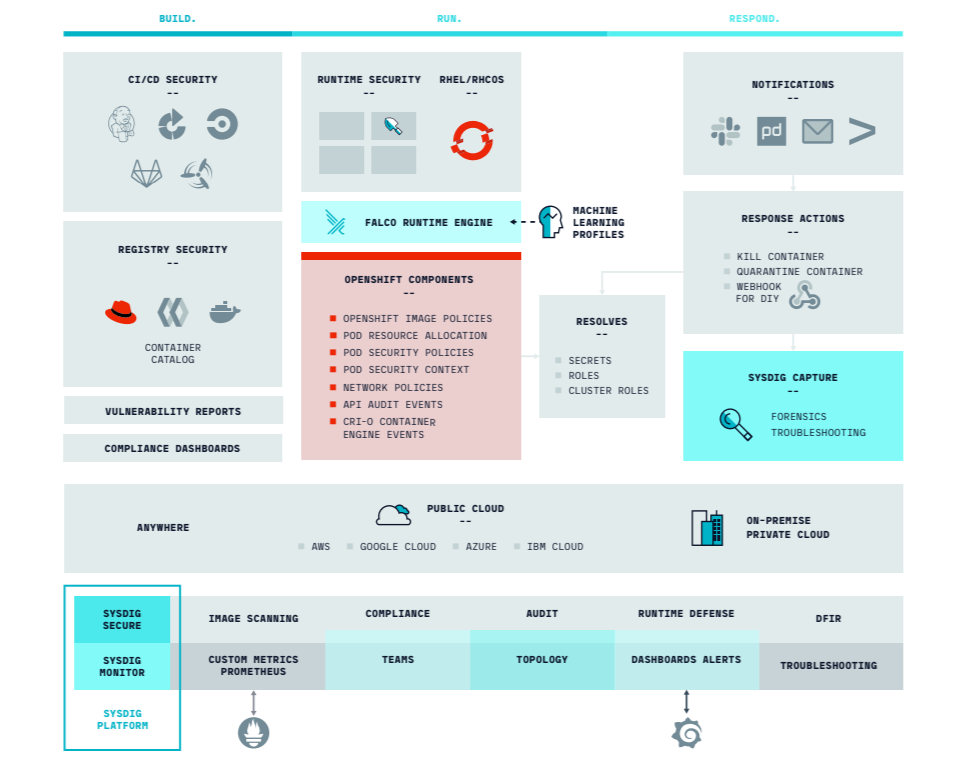
Sysdig takes a layered approach to the way security is applied to an OpenShift environment. There are distinct phases in the way applications are created and distributed to a cloud native environment: the build phase, the run phase and the response phase.
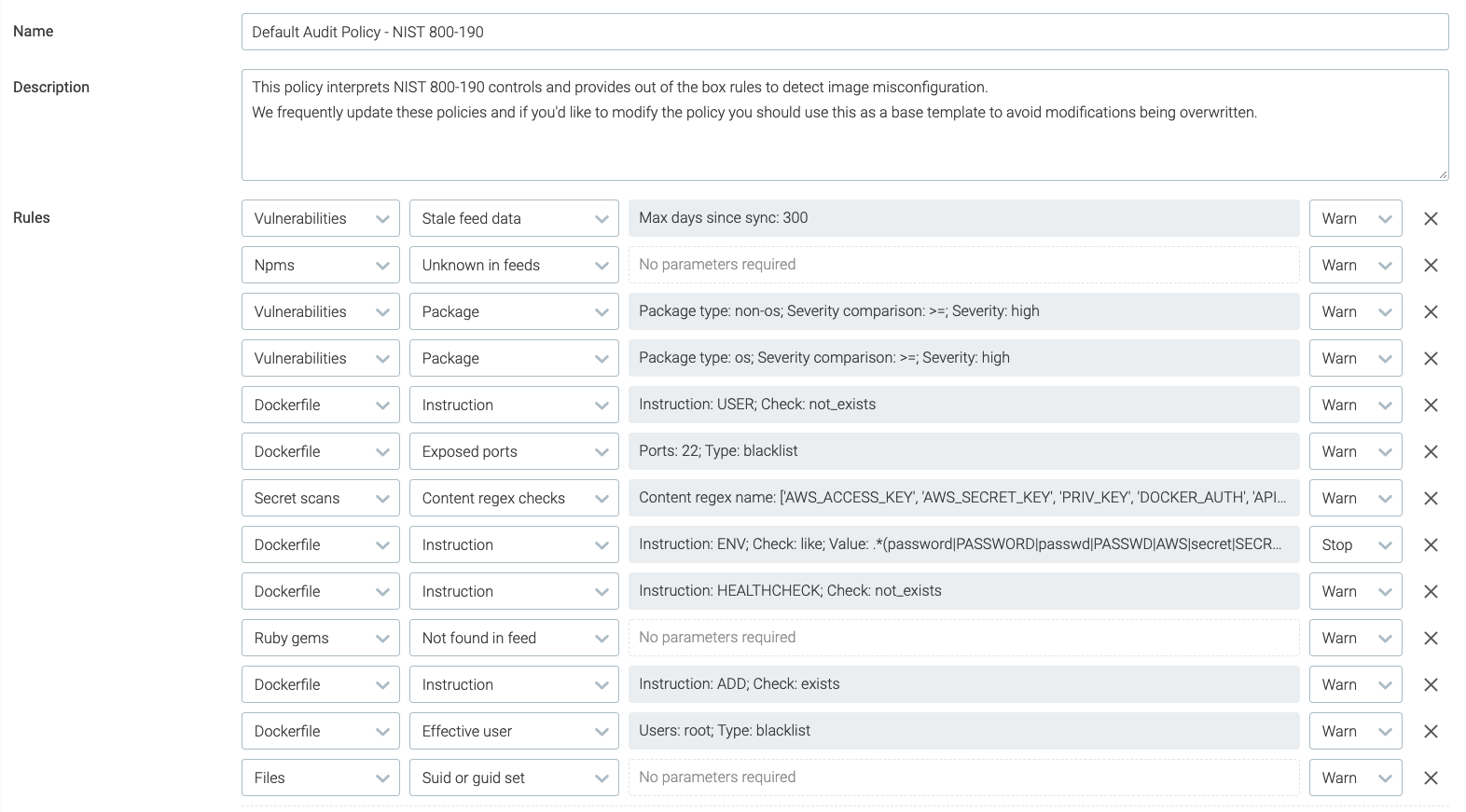
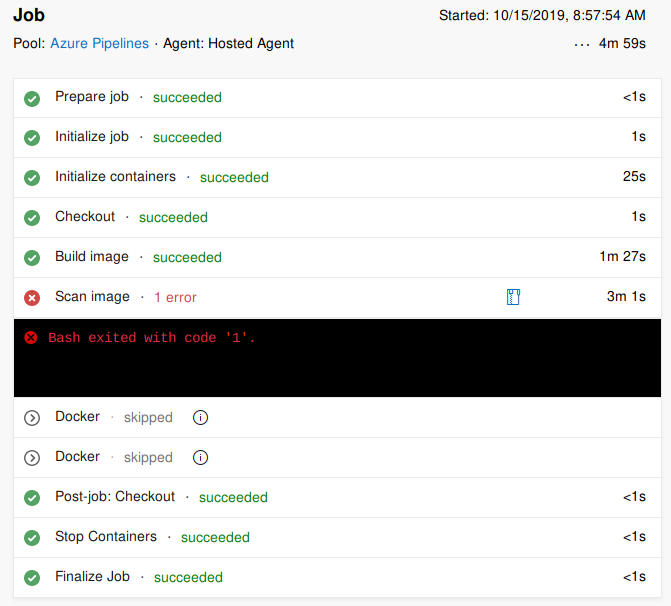
For the build phase, Sysdig Secure integrates with your build pipeline. As part of the build, a call is made which scans the image, the results of which are sent to Sysdig Secure to be evaluated. The criteria for evaluation is decided by policies. These policies have gates that can either warn or stop a build based on the condition set.
Using other Azure services? Complement ARO and beef up your GitOps workflows with Azure Container Registry and pipeline management with Azure Pipelines. Sysdig even has an integration for this.
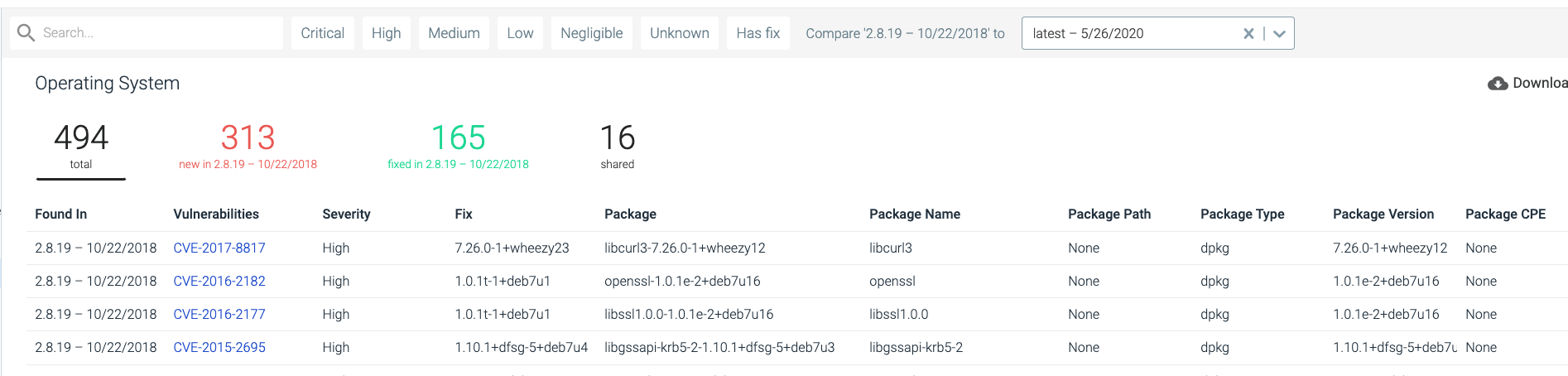
The next layer of this is centered on the run phase. For runtime, Sysdig Secure focuses heavily in three areas: image drift, compliance and runtime detections. By image drift, we mean alerting you in real time when new CVEs appear in existing, running images, or allowing reports to be generated showing where a CVE applies or when critical images need to be remediated. Being able to compare previous images and their vulnerability set to current images (vuln diff) also comes into play here.
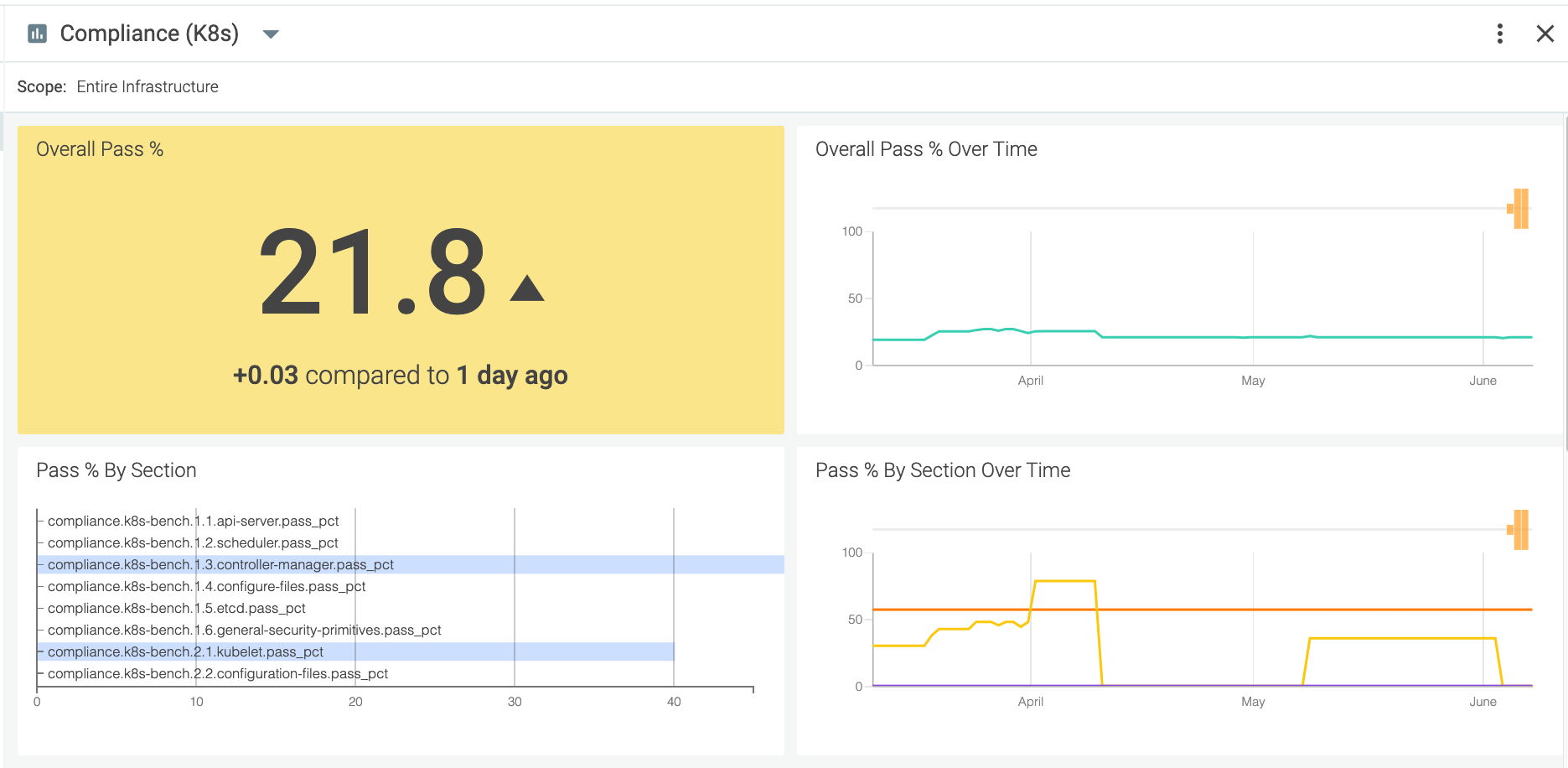
The next step of runtime centers on continuous compliance. Sysdig Secure leverages the CIS Benchmarks for Linux, Kubernetes and Docker to ensure that best practices are being followed to harden the environment as new iterations are spun up and down. Secure then turns these checks into metrics and charts out your compliance with those standards over time.
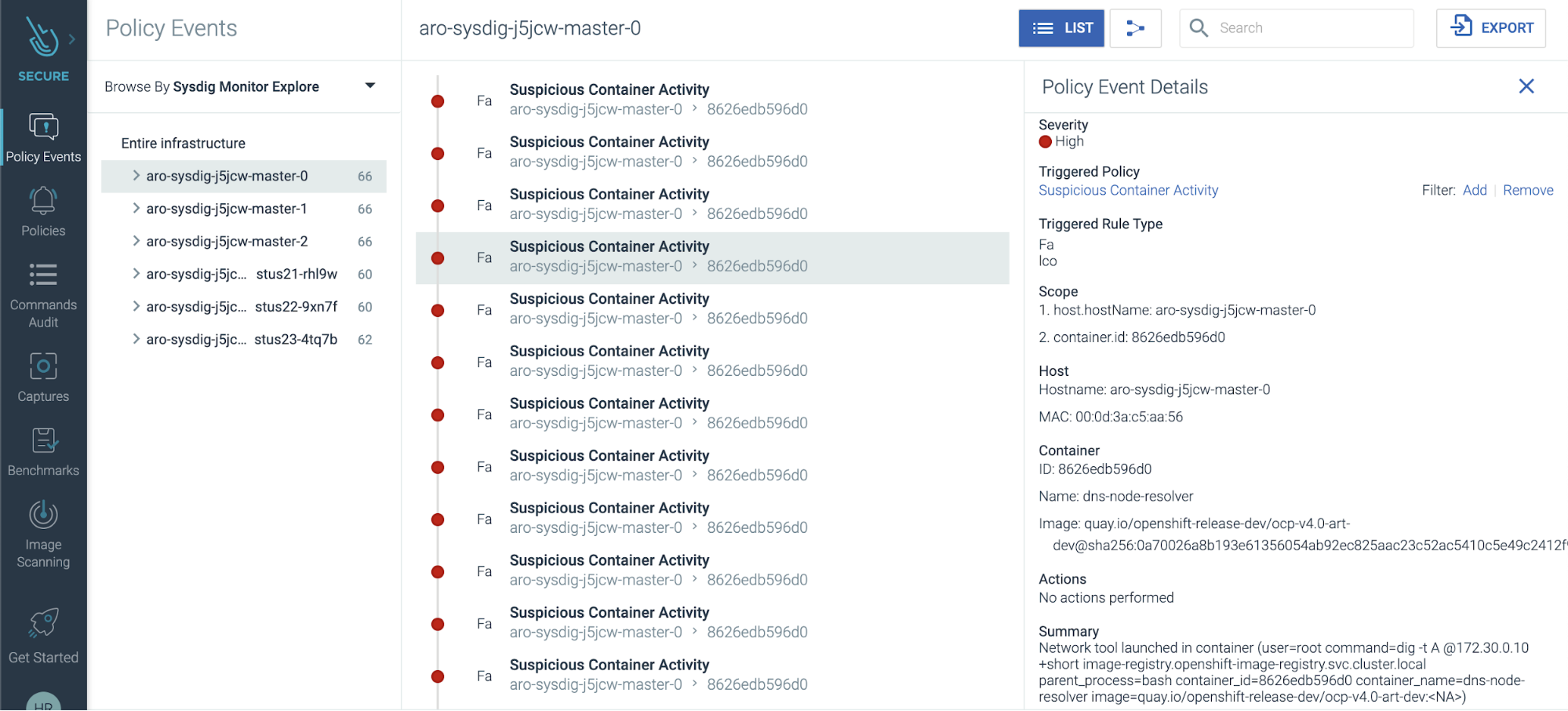
The third pillar in runtime is real-time detection. Sysdig Secure is powered by Falco, the most advanced way to detect threats in real-time. Falco does analysis of kernel calls being made across a host to detect activity. This can be anything from reading a file in a protected location, to executing a shell against a container, or editing a configmap in Kubernetes.
This library of run-time rules allows for an unparalleled ability to detect activity; however, Sysdig Secure also has learning mechanisms in place to detect what a given application is doing in order to build whitelists of activity, all the way down to individual system call activity. Once approved, those become run-time policies allowing Secure to alert/react to undesired or unexpected activity in the OpenShift environment.
How Does ARO and Sysdig Help you confidently run Azure Redhat Openshift?
With these three key features:
- Fully managed solution in collaboration with Microsoft and Red Hat engineers.
- Simplified licensing: no longer manage your own Red Hat subscriptions for OpenShift. ARO is a single subscription that covers the availability, upgrade and functionality of the OpenShift platform and subscription management with Red Hat.
- Single Agent provides you with Security and Monitoring for your cluster, using the same context and details you have provided in ARO with a simple one click!
Conclusion
In this article, we provide you with guidance on deploying Redhat on Azure with concrete examples along with a potent tool to add additional visibility, security and troubleshooting in a single agent. You can now have confidence in your Azure Redhat Openshift deployment and be able to utilize these tools as a requirement to satisfy your team’s objectives. Deploy a cluster today and install Sysdig!
Sysdig, as part of this blog, is providing a FREE 30-day trial of Sysdig.
Sysdig’s OpenShift Security guide, which was written with Red Hat and Sysdig specialists, offers even more details on how Sysdig can help secure your ARO cluster(s).
Thank you to Hart Ripley from Arctiq for all the help contributing to this document! Arctiq is a services-led firm providing expertise in the new world of IT transformation. We help clients build continuous improvement strategies using automation, orchestration, DevOps methodologies, security, and customized workflows. https://www.arctiq.ca/ for more details.