MITRE ATT&CK is a comprehensive knowledge base and complex framework of over 200 techniques that adversaries may use over the course of an attack. While MITRE’s full ATT&CK framework is publicly available, it can be characterized into 3 key elements:
- Tactics – represent the “why” of an ATT&CK technique. It is the adversary’s tactical objective: the reason for performing an action.
- Techniques – represent “how” an adversary achieves a tactical objective by performing an action. For example, an adversary may dump credentials to achieve credential access.
- Procedures – are the exact ways a particular adversary or piece of software implements a technique. These are described by the examples sections in ATT&CK techniques.
In short, MITRE has analyzed all of the tactics, techniques, and procedures (TTPs) that advanced threat actors could possibly use in their attacks and separated them into 11 categories.
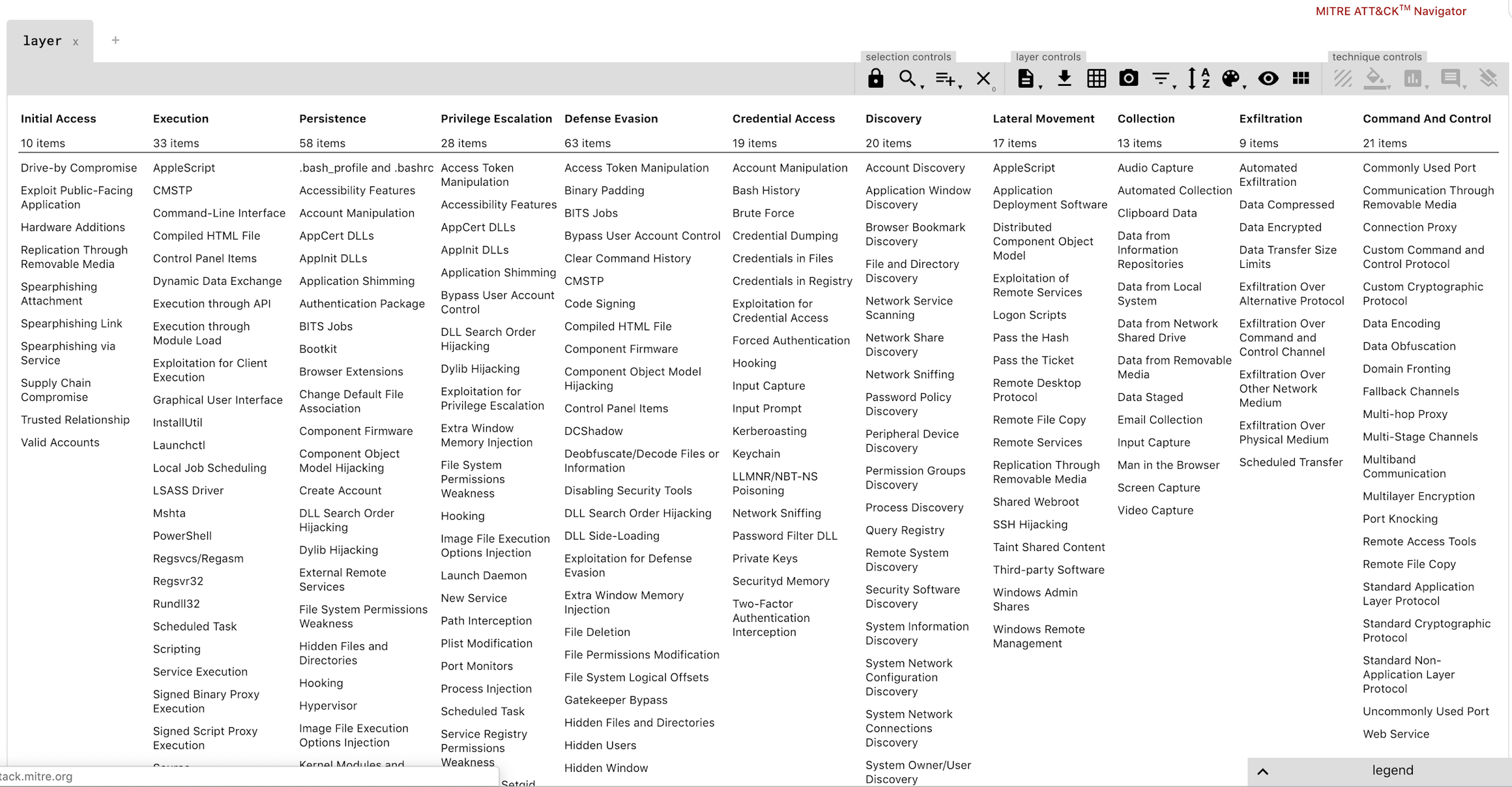
Execution: The execution tactic represents techniques that result in execution of adversary-controlled code on a local or remote system.
Persistence: Persistence is any access, action, or configuration change to a system that gives an adversary a persistent presence on that system.
Privilege Escalation: Privilege escalation is the result of actions that allows an adversary to obtain a higher level of permissions on a system or network.
Defense Evasion: This consists of techniques an adversary may use to evade detection or avoid other defenses. Sometimes these actions are the same as or variations of techniques in other categories that have the added benefit of subverting a particular defense or mitigation.
Credential Access: Represents techniques resulting in access to or control over system, domain, or service credentials that are used within an enterprise environment.
Discovery: This consists of techniques that allow the adversary to gain knowledge about the system and internal network.
Lateral Movement: This consists of techniques that enable an adversary to access and control remote systems on a network and could, but does not necessarily, include execution of tools on remote systems.
Exfiltration: This refers to techniques and attributes that result or aid in the adversary removing files and information from a target network.
Falco rules based on MITRE ATT&CK framework.
Falco is an open source, container security tool designed to detect anomalous activity in your containers. Falco taps into system calls to generate an event stream of all system activity. Falco’s rules engine then allows you to create rules based on this event stream, allowing you to alert on system events that seem abnormal. Falco’s rich language, allows you to write rules at the host level and identify suspicious activity.
Falco now provides rules that are focused specifically on containerized environments (total of 46 and growing) and adhere to 8 key MITRE frameworks. The below table summarizes these rules. Click on any Falco rule in the corresponding section to learn more.
Falco MITRE Rule Matrix
To learn more about Falco, visit the homepage or get started on github!

