Sysdig, an industry leader for monitoring and security of cloud-native workloads, and IBM have joined forces to bring a fully Integrated powerful platform that delivers the security and performance that enterprises need in today’s multi-cloud world.
Sysdig Secure and the IBM Cloud Pak for Multicloud Management can help you accelerate Kubernetes and cloud adoption by addressing security and regulatory compliance from the start on enterprise hybrid cloud environments. As more and more organizations go multi-cloud, standardizing the management, security and monitoring of workloads, wherever they may run, helps to smooth operations.
Applying governance capability of IBM Cloud Pak for Multicloud Management to operate Kubernetes and hybrid clouds for enterprise security standards. Click to tweetIBM Cloud Pak for Multicloud Management centralizes visibility, governance and automation for containerized workloads across clusters and clouds into a single dashboard. One of its key capabilities is the centralization of security findings to help cloud teams’ admins understand, prioritize, manage and resolve security issues that are related to their cloud applications and workloads. The integration of Sysdig Secure with IBM Multicloud Management extends the depth of security intelligence available to their users with:
- Container image vulnerability management and configuration validation.
- Runtime security with prevention, threat detection and mitigation.
- Incident response and forensics.
- Compliance and audit.
Sysdig Secure increases IBM Cloud Pak for Multicloud Management compliance capabilities to help meet regulatory requirements like NIST, PCI, GDPR or HIPAA. By deploying Sysdig Secure with IBM Cloud Pak for Multicloud Management, users can extend container security to prevent vulnerabilities, stop threats, accelerate incident response and enable forensics.
Sysdig Secure: Cloud native security
Sysdig Secure, part of the Sysdig Secure DevOps Platform, is a Kubernetes security and compliance solution for securing cloud-native workloads. It embeds security intelligence into the build, run and response stages of the container lifecycle.
Sysdig Secure features:
- Hybrid cloud capabilities beyond Kubernetes, supporting public and private OpenShift, and other flavors including managed Kubernetes service from different cloud providers.
- Detection, prevention and reporting of vulnerabilities with image scanning.
- Runtime security event detection via Falco engine rules, with machine-learning-based profiling and extensive out-of-the-box detection patterns.
- Remediation actions for threat blocking by pausing or killing containers, forwarding events to SIEM or executing your own security playbook.
- Security enforcement through Kubernetes native controls like PSPs.
- Incident response and container forensics with Activity Audit and Sysdig captures.
- Compliance and regulatory audits with CIS benchmarking, PCI and NIST controls, MITRE ATT&CK framework, etc.
IBM Cloud Pak for Multicloud Management: Hybrid cloud Kubernetes governance
IBM Cloud Pak for Multicloud Management enables you to oversee multiple Kubernetes and OpenShift clusters regardless of where they run. It provides a single dashboard for viewing and managing your clusters across both public and private clouds, and can be deployed on IBM Cloud, IBM Cloud Private or Openshift as CloudPak.
With IBM Multicloud Management, you have control of your Kubernetes clusters from a single point. It provides user visibility, application-centric management (policy, deployments, health, operations), and policy-based compliance, including several out-of-the-box policy templates for various security controls, such as CIS, across cloud providers and clusters. This helps you ensure that your clusters are secure, operating efficiently and delivering the service levels that applications expect.
The multicloud management architecture consists of a hub cluster, used for management, and a set of managed clusters. A klusterlet agent runs in every managed cluster to communicate with the hub, providing feedback and applying required commands on the managed clusters.
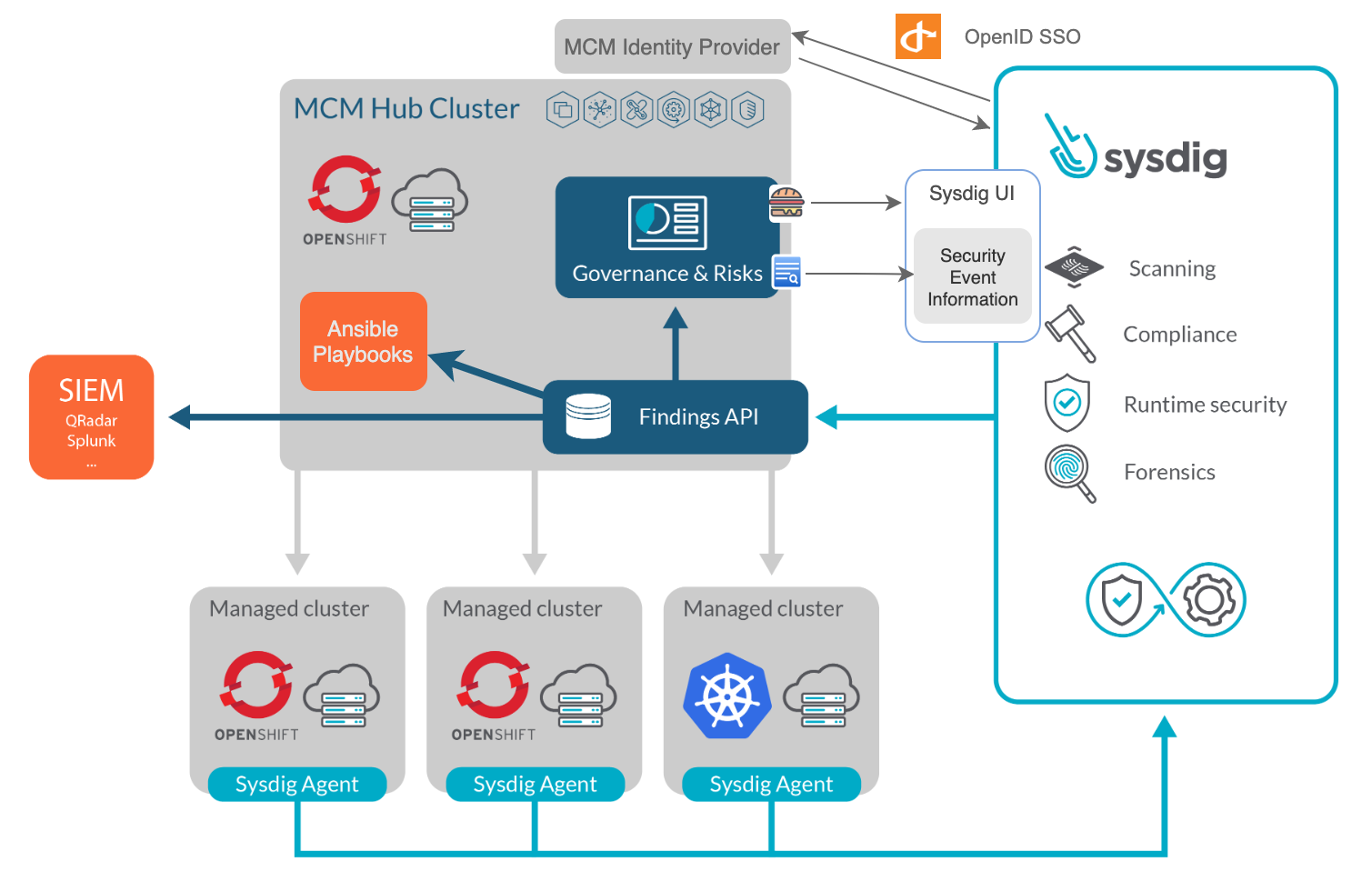
IBM Cloud Pak for Multicloud Management allows you to trigger actions targeting any of the managed clusters. You can, for instance, create resources from a YAML definition, like an OPA policy configmap or a PSP. Or, select Helm charts from the Catalog to quickly deploy applications to multiple clusters at once right from the multicloud management Dashboard, API or CLI tool.
Extending detection with Sysdig Secure findings and threat blocking
Centralized access to security events is critical for CISOs and SREs to understand and address incidents occurring across cloud deployments in real-time. The governance and risk dashboard in IBM Cloud Pak for Multicloud Management provides a centralized view of policies, violations and security findings to accelerate visibility into security threats. It has out-of-the-box rules to simplify policy definition and displays any non-compliance status in the Policies section.
In the Security findings section, you get an aggregated and searchable view of occurrences coming from all managed clusters as well as non-compliance items from the Policy controllers running in the clusters. These findings are summarized by severity, categories or standards, and can be optionally grouped by cluster.
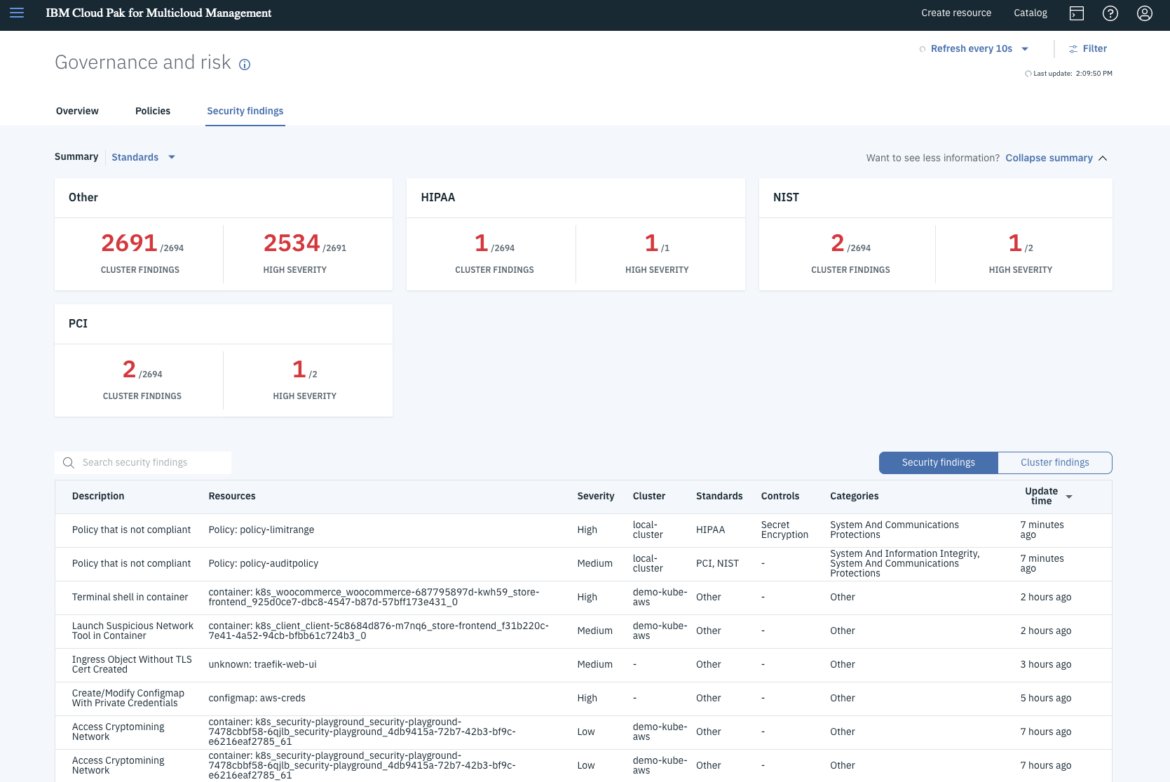
The Security findings section of the dashboard is backed by the Security Findings API (similar to the Grafeas API), which enables IBM Cloud Pak for Multicloud Management to incorporate additional finding sources, like those provided by Sysdig Secure. Security Findings can generate audit logs that can be forwarded to SIEMs, such as IBM QRadar and Splunk, for visibility and to drive remediation of such findings for the security operations center (SOC).
Runtime threat detection in action
After enabling IBM Cloud Pak for Multicloud Management integration in Sysdig Secure, you will start receiving Policy events on the Security findings UI that are generated by the policies and rules enabled on your Secure account. These items are not just available in the UI, but they are also stored in the findings database, which can be further integrated with SIEM tools used by enterprise Security Operations Center teams, as well as governance, risk and compliance tools used by enterprise risk and compliance teams.
The combination of Sysdig generated security events with other findings within IBM Cloud Pak for Multicloud Management provides a more holistic view of your security posture. You can see some event examples in the following screenshot:
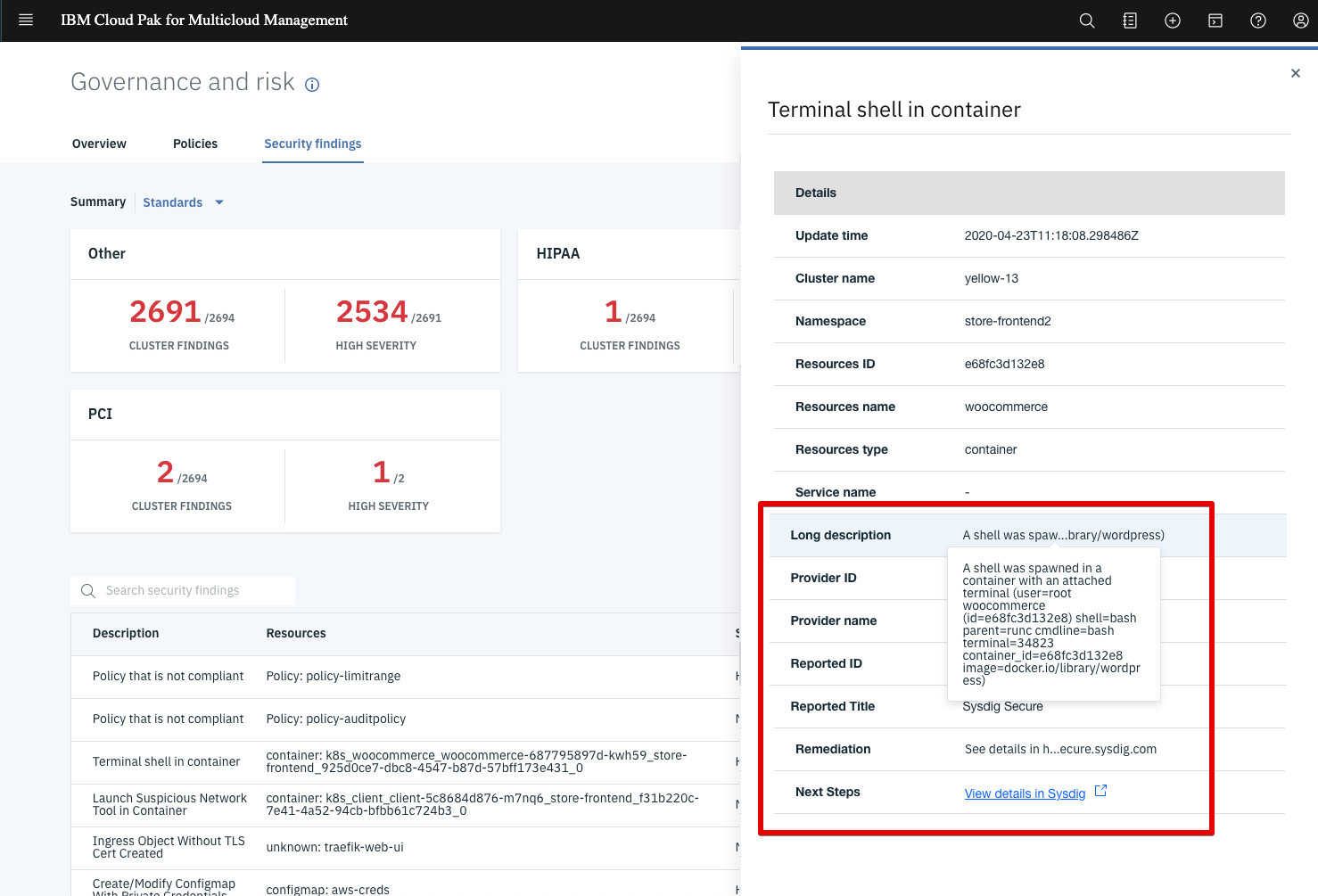
In the list at the bottom, you can see a table with sortable columns and multiple rows. Each row contains the most important event fields at a glance, like description, associated resource, severity, cluster name, standards, controls and categories, as well as the time the event happened. In this view, we can see:
- A couple of “Policy that is not compliant” events coming from multicloud management Policies.
- “Launch Suspicious Network Tool in Container” (exfiltration and discovery) and “Terminal shell in container” (Command-Line Interface execution) runtime events, included in MITRE ATT&CK knowledge base of adversary tactics and techniques and detected by Sysdig Secure’s Falco engine,
- Another couple of events from Sysdig Secure rules that watch the Kubernetes Audit Log, like an “Ingress Object Without TLS Cert” (PCI 4.1 – Strong cryptography for sensitive data) or a ”Configmap with Private Credentials” (NIST SP 800-190 3.3.2).
Clicking on any of these items opens a detailed view. In this example we see a “terminal shell being spawned in a container” runtime event forwarded from Sysdig Secure. We can see that the security event occurred at the demo-kube-aws cluster, and additional context information shows metadata like the Kubernetes namespace and container name. The long description field contains even more information like the username, process name and image.
For further incident response and forensics investigation, you can click the link to “view details in Sysdig” in the security findings detail section, and jump into the Sysdig Secure UI to explore deeper details of the event:
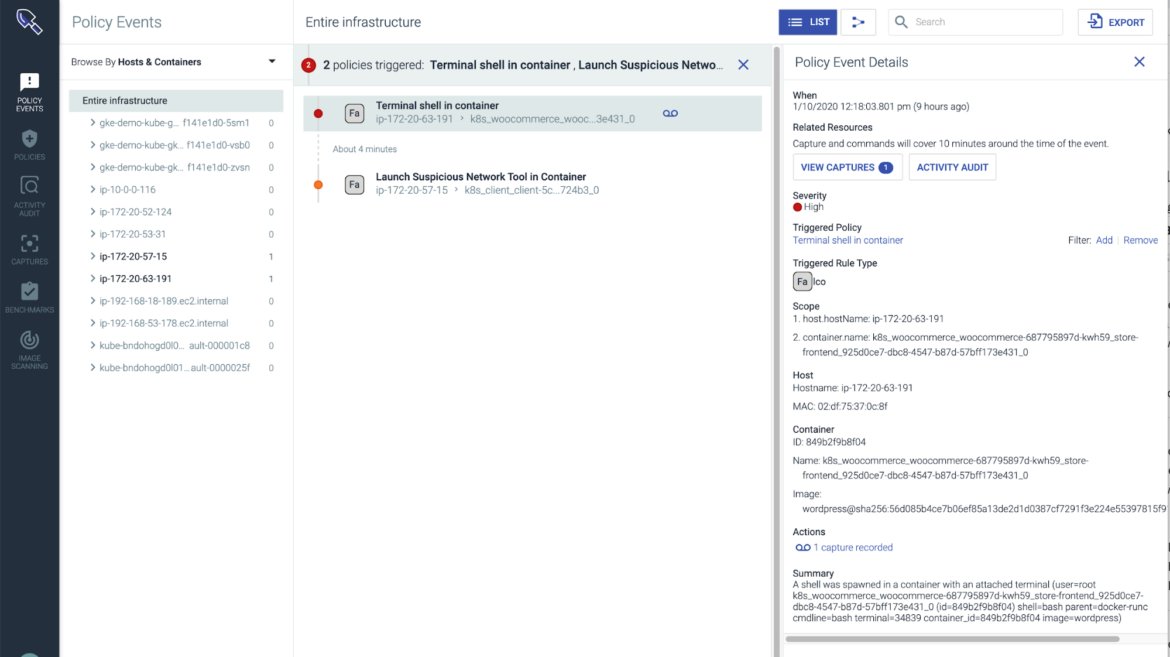
Now you can dig deeper by checking the Activity Audit and perform a post-mortem analysis, correlating all the activities from the same context in a timeline to find the Kubernetes user that launched the shell along with the activity that happened inside that terminal session:
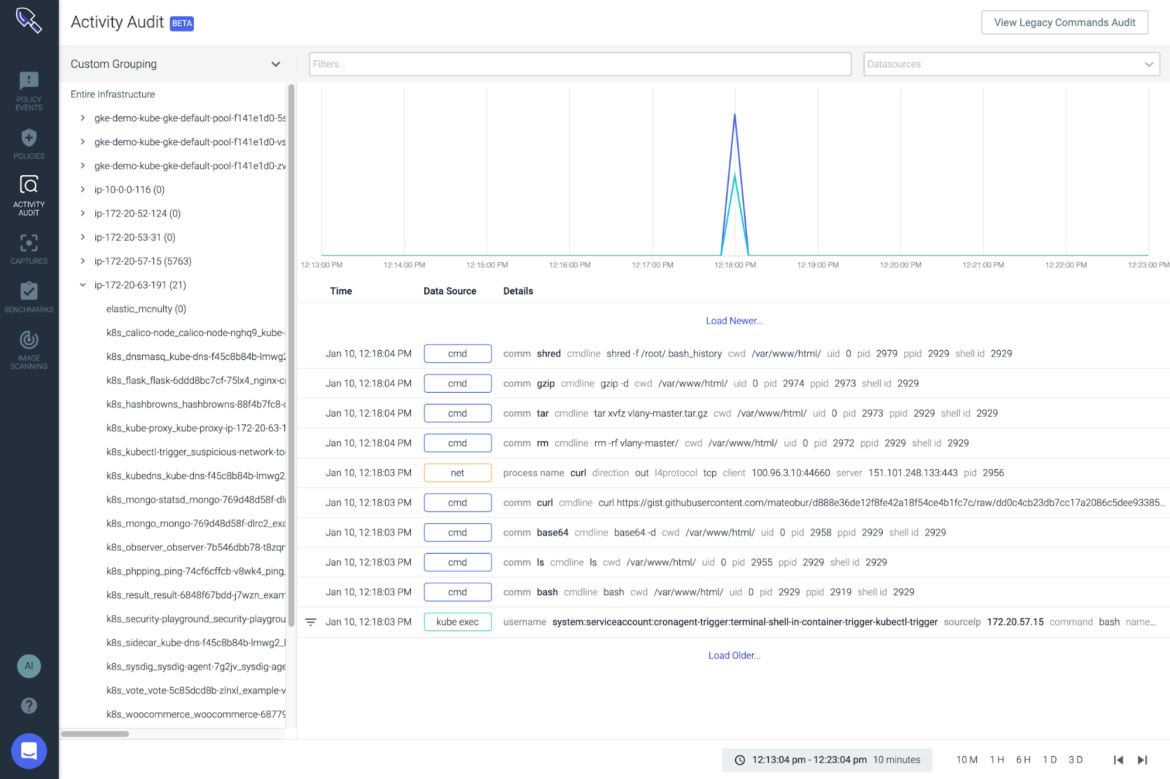
If the Runtime Policy that you created included triggering a capture file, you can also analyze the detailed capture information directly from the UI. This lets you inspect metrics, executed commands, system calls, sockets and files, and even examine I/O streams to check the data that was transmitted, read or written during the incident:

Watch this video to see more
Conclusion
The integration of the Sysdig Secure DevOps Platform with the IBM Cloud Pak for Multicloud Management provides enhanced security intelligence that extends threat prevention, detection and response with multicloud management. The addition of in-depth cloud insights with Sysdig means CISOs, SREs and DevOps professionals are able to ensure comprehensive security governance to reduce business risk.
Sysdig and IBM are continuously working on improvements, so expect new features and posts in the near future.


